
WordPress is a powerful web application and is used by up to 43% of the internet, to date. But with great popularity comes great threats. With numbers like these, many would-be attackers are constantly on the lookout for weaknesses in your site — a good reason to implement these WordPress security best practices, right now.
WordPress security best practices
Sans the usual best practices — like keeping your core files, theme(s) and plugins up to date — there are also many other factors to take into consideration. File and directory permissions, and more are necessary to keep safe that which you’ve worked hard on and treasure.
1. Update file permissions
The default file permissions for all files on a WordPress site are typically set to 644. The default directory permissions are set at 755. There are scenarios that warrant differences.
For instance, it is a good idea to have your wp-config.php file set to permissions stronger than 644.
I know of folks who set that file’s permissions to 440. This helps make it harder for the riff raff to access the file. Some people set theirs to 600. That’s fine too.
You can change the file and directory’s permissions via File Manager, in your hosting plan. You can also alter these permissions in your favorite FTP program.
2. Disable the xmlrpc.php File
What is this file? Well, simply put, the XMLRPC is a system that allows for remote updates to WordPress from other applications. To make sure your site stays secure, it’s a good idea to disable xmlrpc.php completely.
However, if you need some of the functions necessary for remote publishing and the Jetpack plugin (for instance), you should use a workaround plugin that allows for these features while still fixing all the security gaps.
One plugin that comes to mind is called Disable XML-RPC. This plugin uses the built-in WordPress filter xmlrpc_enabled to simply disable the XML-RPC API on a WordPress site. This renders it unobtainable by someone looking to compromise your site.
Another plugin that comes to mind is the Disable XML-RPC Pingback plugin, which lets you disable just the pingback functionality. This means that you will still have access to other features of XML-RPC if you need happen to need them — for instance, if you’re running Jetpack. There are other plugins that will also disable this file. See below for more details on that plugin.
Both plugins are easy to use. You just have to install and activate them. They do the rest for you.
In the event that you want to have more control over how the XMLRPC plugin works, you can instead install the REST XML-RPC Data Checker plugin. Once installed and activated, you would just need to go to Settings > REST XML-RPC Data Checker, and then click the XML-RPC tab.
Once there, you will be able to navigate through the interface to better control the xmlrpc.php file and what it does.
If you already have a ton of plugins and want to avoid installing yet another, you can control the xmlrpc.php file via the .htaccess file by adding this line to it:
add_filter( ‘xmlrpc_enabled’, ‘__return_false’ );
That will just turn it off altogether.
You can also edit the .htaccess file with this command:
<Files xmlrpc.php>
Order Allow, Deny
Deny from all
</Files>
Or have your hosting provider disable the file itself.
3. Hide your sensitive details
Once you’ve got your site all dialed in and live, hide certain details from the public eye that might lure someone towards wanting to compromise all your arduous work. A nice plugin for this is called Hide My WP Ghost. This plugin is a paid plugin, but it’s worth the coin, and it’s on sale now for a 5-pack license.
This plugin does a fantastic job of hiding your core files, file paths, login page, and more. It performs the following functions, to name just a few:
- Change the wp-admin and wp-login URLs
- Change lost password URL
- Hide /wp-login path
- Disable XML-RPC access
- Change URLs using URL Mapping
- Weekly security checks and reports
- Email support, and more
4. WAF/CDN protection
A big step towards protection is blocking people you don’t want to have access to your site, altogether. This can be accomplished via a WAF (web application firewall) combined with a CDN (content delivery network).
Fortunately, GoDaddy offers this type of protection through Sucuri. Once purchased and set up, you can go into the firewall settings and enable GeoBlocking, if you so desire, and block entire countries from accessing your site.
The WAF will also help to speed up your site, since it does a wonderful job of blocking the known bad IPs and allowing the good ones to access your site.
5. Combat comment Spam
Another nuisance is comment form spam. There is a great way to limit or prevent this type of problem. The method I like is to utilize the plugin called wpDiscuz.
With this plugin, wpDiscuz will take over your site’s commenting and check against a host of bad actors, filtering out bad or malicious comments by forcing the commenter to enter credentials to comment. You get an email sent to you with each successful comment on your site, so you can then moderate further, if needed.
6. Enable CAPTCHA
It is highly recommended that you also enable CAPTCHA on all forms on your site(s). This will aid in the prevention of form spam. There are several types of CAPTCHA additions out there. Some ask the user to solve a math equation, some have a puzzle to solve, others have you select a series of pictures, and there are more variations.
7. Enable 2-factor authentication (2FA)
A tried-and-true way of keeping out the knuckleheads out there who would seek to do your site harm is to enable 2-factor authentication on every user of your site. If you are on your site all the time, it can be a mild inconvenience to have to enter the 2FA each time you log in. But that is a small price to pay for the security of your site.
A good plugin that can be used to enable 2FA is Wordfence. Just install the plugin and go to this article to see how to enable it.
8. Change the WP-admin URL
The default admin URL has been the same, on WordPress, for years. All bad actors know it and routinely attempt to gain access to your site via said URL. The above mentioned Hide My WP Ghost plugin does a great job of obscuring this URL by simply changing it.
9. Add server-level protection
If your WordPress site is hosted on a server, you can enable other security features that will help keep your site safe. One such feature is in WHM. You can help prevent or limit the possibility of an AnonymousFox compromise by simply turning off Reset Password for cPanel Accounts and Reset Password for Subaccounts.
Simply go to WHM > Tweak Settings > search for password. From there, for the Reset Password for cPanel Accounts and Reset Password for Subaccounts features, select Off. This will help in preventing a bad actor from accessing — and then changing — the cPanel and subaccounts passwords.
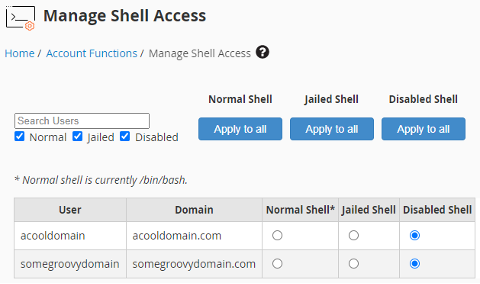
The second thing you’ll want to do, if your site is hosted on a server, is to disable shell access to all your cPanel accounts. Just go to WHM > Manage Shell Access > Disable Shell for all cPanel accounts.
10. Strong login credentials
Last among our WordPress security best practices, but certainly not least, always use strong passwords and obscure usernames. I can’t tell you how many times I’ve come across passwords like Password123!. Another common mistake is making the username something relative to the site itself.
If you want to get compromised, that is a sure-fire way to do it.
Long and randomly generated passwords, in conjunction with usernames that have nothing to do with the site, are always your best combo.
Another great idea is to continually change your passwords. It might seem like a pain, but that pales in comparison to getting hacked. How often you change your passwords is up to your discretion. — just as long as you do. (You’ll be glad you did.)
Closing thoughts on WordPress security best practices
All in all, you have worked so hard for your intellectual property (or your client’s). Why not keep it safe? These few, but helpful, WordPress security best practices can go a long way toward a successful and compromise-free website for years to come.