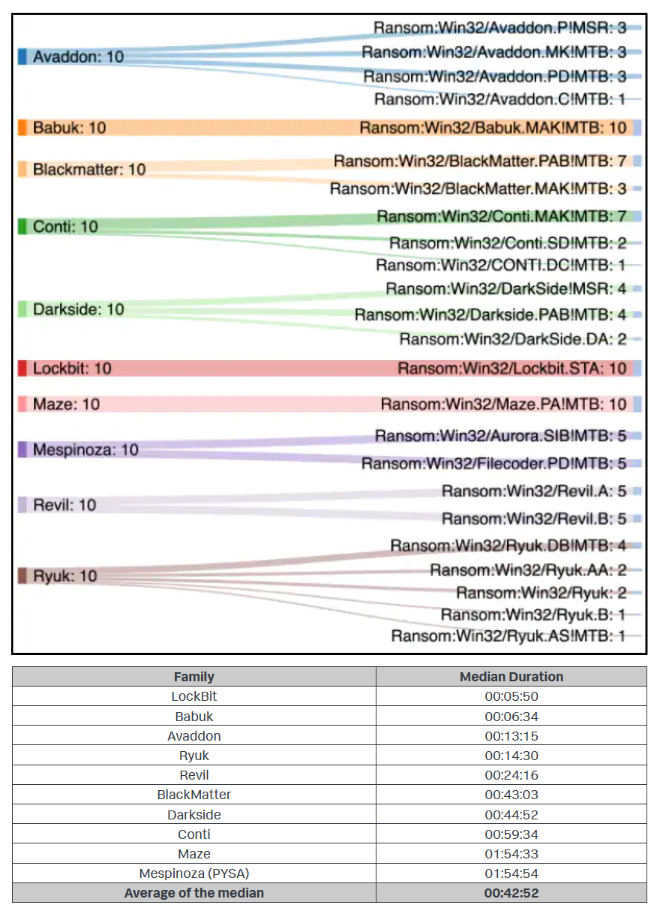
Why it matters: For IT admins and cybersecurity teams, a ransomware attack is a crucial race against time to detect and contain damage while salvaging what’s left of a company’s data assets. But how much reaction time is there when such an incident occurs? Not a lot it seems, as revealed by ransomware testing of ten candidates, where LockBit led the pack by encrypting nearly 100,000 files on a Windows Server machine in just over four minutes.
The ransomware encryption speed test conducted by Splunk involved ten samples from ten ransomware families, which were run on four different ‘victim’ profiles. From a total of 400 test runs, a sample from LockBit running on a Windows Server 2019 machine emerged as the fastest ransomware, encrypting all 53GB of test data in just four minutes and nine seconds.
This test data consisted of 98,561 files, comprising pdfs, and excel and word documents. Meanwhile, the ransomwares were tested on a Windows 10 and Windows Server 2019 machine and included samples from REvil, Darkside, Babuk, Maze, LockBit, and several others. LockBit not only had the fastest sample, but also came out first overall in terms of median duration.
The interestingly named ‘Babuk’ ransomware emerged second overall, though it had its reputation spoiled somewhat by having the slowest individual sample that took over three and a half hours for file encryption.
Splunk also shared a whitepaper (requires a business email to download), offering a comprehensive look at this research. As for strategies to adopt in case of a ransomware attack, the company advises using multi-factor authentication, network segmentation, centralized logging, and keeping systems patched.